AKASH SONG
oNLY FoR YoU ..
how to real hack

We like hacking and security.If You Have new Hacking Tricks Which You Want To publish
Don't Tease The Hacker

Our Slogan: Hack the Cracker
Blue Screen Error- How to Fix it.
Blue Screen = The Most Irritating Error Face by Windows Users. Did you ever got stuck with this type of Error ?
Most of will answer it YES.
What is Blue Screen of Death (BSOD) ?
Blue screen of death is nothing but an error Shown in Microsoft Windows Operating Systems which Stops Further Operations.
Why BSOD Error is Caused ?
This error is Generally Hardware or Drivers Related.causing the Computer To stop Responding And prevents Damage to the Hardware And data.
BSOD Looks Like the Below Picture. Manny Windows Users Must be Familiar With This.
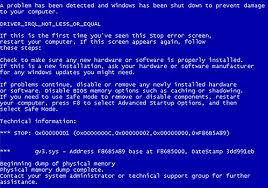
How To Fix BSOD :
As I said There are several Reasons For BSOD, Unfortunately There is no Particular solution but The Following Tips And tricks Can Help you To get Rid Of it.
1. Remove Startup Programs That Starts Will System Booting.
What happens is when you System Boots, Many Other apps try To load at the same time whill may result in to BSOD. so Remove Unwanted Programs On startup.
How To Remove :
Press Windows Key +R
Run Box will appear. Type "msconfig" and Hit Enter,
Click on Startup Tab and remove all Unwanted Programs and click on apply.
It may ask you to restart your syste, So restart it .
Removing programs at startup will fix your problem.
2.Uninstall Softwares:
Many Times while installing a softare A blue screen occors with a message that says, The Software that you are installing is Culprit . Verify all the changes that you made to your system and reset Them. Uninstall the installed Application it will help you to a great extent.
3. Resetting your Hardwares And Drivers :In some cases Due to Faulty Hardware connection it show the blue error screen. You can prevent this by ensuring you all hardware connection such as external ports,motherboard pins are set correctly.Bad drivers may also cause the same problem.Keep your drivers up to date.
Above tips will definately help you to get rid of Bluescreens.
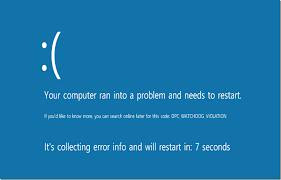
Windows 8 users May have Experienced a New Blue screen:
In windows 8 it will Tell you About the error and sad Emoticon At the top of the text .
Same as below pic.
Most of will answer it YES.
What is Blue Screen of Death (BSOD) ?
Blue screen of death is nothing but an error Shown in Microsoft Windows Operating Systems which Stops Further Operations.
Why BSOD Error is Caused ?
This error is Generally Hardware or Drivers Related.causing the Computer To stop Responding And prevents Damage to the Hardware And data.
BSOD Looks Like the Below Picture. Manny Windows Users Must be Familiar With This.

Img src= google
As I said There are several Reasons For BSOD, Unfortunately There is no Particular solution but The Following Tips And tricks Can Help you To get Rid Of it.
1. Remove Startup Programs That Starts Will System Booting.
What happens is when you System Boots, Many Other apps try To load at the same time whill may result in to BSOD. so Remove Unwanted Programs On startup.
How To Remove :
Press Windows Key +R
Run Box will appear. Type "msconfig" and Hit Enter,
Click on Startup Tab and remove all Unwanted Programs and click on apply.
It may ask you to restart your syste, So restart it .
Removing programs at startup will fix your problem.
2.Uninstall Softwares:
Many Times while installing a softare A blue screen occors with a message that says, The Software that you are installing is Culprit . Verify all the changes that you made to your system and reset Them. Uninstall the installed Application it will help you to a great extent.
3. Resetting your Hardwares And Drivers :In some cases Due to Faulty Hardware connection it show the blue error screen. You can prevent this by ensuring you all hardware connection such as external ports,motherboard pins are set correctly.Bad drivers may also cause the same problem.Keep your drivers up to date.
Above tips will definately help you to get rid of Bluescreens.
Windows 8 users May have Experienced a New Blue screen:
In windows 8 it will Tell you About the error and sad Emoticon At the top of the text .
Same as below pic.

akash ............Use Whatsapp on PC for Windows and also Mac .......akash
Whatsapp is the most Popular Messanger available in the Market for Mobile Phones.
Unfortunately if you dont own a Smart phone then you might not be able to use whatsapp. But don't worry today we Will learn How to use Whatsapp On PC as well.
You can Use it On both Windows and Mac.
Unfortunately if you dont own a Smart phone then you might not be able to use whatsapp. But don't worry today we Will learn How to use Whatsapp On PC as well.
You can Use it On both Windows and Mac.

Let us See How to Use Whatsapp On Windows and Mac PC.
To Run Whatsapp on Pc, We will Require Android Emulator, Android Emulator Helps us to Run Whatsapp on PC.
Step 1: Youwave And Bluestack Are the Two Android Emulator which enable us to Run Whatsapp or any other Android App on PC.
Step 2: If you Go for Bluestack then Download and install it, then run the Bluestack and Click
on " Apps "
Then Click on the Tab " Social " and select " Whatsapp " and Install it.
Step 3: If you Go for Youwave which I am Using On My PC then just download and install.
Now download Whatsapp.apk and move the downloaded file to PC directory.
To Check PC's Directory, Open Youwave click on help > Instruction. Now move your
whatsapp.apk file in to that directory . Then Click on View then Redraw Icons.
Now You will see Whatsapp icon .
After Installing Whatsapp on Youwave or Bluestack you have to enter
Mobile number which is not used earlier For Whatsapp account. Then they
will take 5 Minutes to verify and will send you Code.
Enter that code and thats all.
Enter that code and thats all.
The Sony Wrist Computer Concept for the Year 2020
Considering the rate at which technology is developing by leaps and
bounds, the proposition of having a mini computer strapped to your wrist
does not seem to be a distant probability. However, there is one
concept design of a wrist band converting into a PC which has completely
caught the imagination of the avid gadget aficionado- the Sony Nextep
Computer that has been designed by Hiromi Kiriki. Although, this
fabulous design is in its concept stage, nevertheless its entire form,
idea and features have made it one of the most awaited gadgets to come
out nearly seven years from now!

This concept of a wrist computer would be having an OLED touch screen
which would be extremely flexible and that would be accompanied with a
holographic projector that would do away with the screen and make it
very high-tech. You can pull out additional keyboard panels from the
device and the features would also connect you to your preferred social
networking sites.

This wearable PC might sound a little geeky, but that is the way things have always been imagined. Think of how we might have sounded back in the days before laptops and mobile phones existed! We have now come to an age which is predominantly dependent and run by technology and communication. Hence, our need for internet connectivity is at all times and this is the reason why technology needs to evolve further and provide us more profound devices that enable us to remain ‘connected’ at every step of the way- this is why Nextep Computers would bring about a new revolution in technology.

The design is super cool as it looks like a bracelet and is worn like one too. This potential computer by Sony raises a lot of hopes as its design is very capable of supporting various apps along with other user friendly features like the holographic screen and the retractable keyboard- which combines both the qualities of a high-end PC as well as a mobile phone. The bracelet device can be converted into a tablet with three display units and two additional keyboard panels, however, it is not ascertained whether it would also double up as a mobile device, although there is a high probability that it might.
This should be the next big thing in technology that is being brought about by the electronics giant Sony which has risen hopes of the Sony Nextep as being the next big thing in the technology market!
This wearable PC might sound a little geeky, but that is the way things have always been imagined. Think of how we might have sounded back in the days before laptops and mobile phones existed! We have now come to an age which is predominantly dependent and run by technology and communication. Hence, our need for internet connectivity is at all times and this is the reason why technology needs to evolve further and provide us more profound devices that enable us to remain ‘connected’ at every step of the way- this is why Nextep Computers would bring about a new revolution in technology.
The design is super cool as it looks like a bracelet and is worn like one too. This potential computer by Sony raises a lot of hopes as its design is very capable of supporting various apps along with other user friendly features like the holographic screen and the retractable keyboard- which combines both the qualities of a high-end PC as well as a mobile phone. The bracelet device can be converted into a tablet with three display units and two additional keyboard panels, however, it is not ascertained whether it would also double up as a mobile device, although there is a high probability that it might.
This should be the next big thing in technology that is being brought about by the electronics giant Sony which has risen hopes of the Sony Nextep as being the next big thing in the technology market!
akash song video
akashpilu@gmail.com
akashnet@usa.com
akashnet@zmail.com
.........................................................
10 Internet Security Tips for Complete Protection
However, it is still possible to
effectively combat insecurity on the Internet provided that, the users
are well aware of the common scams and frauds and know how to protect
themselves. A study shows that over 91 percent of the Internet users are
unaware of the online scams and are therefore worried about their
security. If you are one among those 91 percent, then this post is just
for you!
10 Tips for Internet Security:
Here is a list of 10 simple Internet security tips to maximize your online protection:
-
Always install a good antivirus software and keep it up-to-date. Also install a good anti-spyware to keep spyware away from your computer.
-
Always visit known and trusted websites. If you are about to visit an unknown website, ensure that you do not click on those untrusted links and banners.
-
Perform a virus scan on the files/email attachments that you download before executing them.
-
Regularly update your operating system and browser software. For a better security, it is recommended that you surf the Internet through the latest version of your browser program.
-
Never share your password (email, bank logins etc.) with any one for any reason. Choose a strong password (A blend of alphanumeric+special symbols) and change it regularly, eg. every 3 months. Avoid using easy-to-guess passwords. (ex. pet’s name or kid’s name)
-
Always type the URL of the website in your browser’s address bar to enter the login pages.
-
Before you enter your password on any login page, ensure that you see https instead of http in your browser’s address bar. Example. https://mail.google.com instead of
http://mail.google.com. HTTPS protocol implements SSL (Secure Sockets Layer) and provide better security than a normal HTTP. For more information on HTTPS and SSL see Know More About Secure Sockets Layer (SSL). -
Beware of phishing emails! Do not respond to any email that request you to update your login details by clicking on a link in the body of the email. Such links can lead to Fake Login Pages (Spoofed Pages). For more information on phishing refer How to Identify and Avoid Phishing Scam. Also refer my other post on How to Protect an Email Account.
-
Always hit the logout button to close your login session rather than abruptly terminating the browser window. Also, clear your web browser caches after every session to remove the temporary files stored in the memory and hard disk of your PC.
-
Avoid (Stop) using any public computers or computers in the Internet cafes to access any sensitive/confidential information. Also, avoid such computers to log in to your email/bank accounts. On a public computer, there is every chance of spyware and malware infections to be present.
By following the above 10 tips, your
Internet security can be guaranteed up to 90 percent. I hope this
information will help my readers for keeping themselves safe from any of
the online insecurities. Cheers! Pass your comments.
Beware of Common Internet Scams and Frauds
INTERNET SECURITY
1. Phishing Scam:
This is one of the most commonly used
scam to steal bank logins and other types of passwords on the Internet.
Phishing is fraudulent process of attempting to acquire sensitive
information such as usernames, passwords and credit card details by
masquerading as a trustworthy entity in an electronic communication.
Phishing is typically carried out by e-mail or instant messaging.
Example: You may
receive an email which claims to have come from your bank/financial
institution/online service provider that asks you to click a link and
update your account information. When you click on such a link, it may
take you to a fake page which exactly resembles the original one. Here,
you’ll be asked to enter your personal details such as username and
password. Once you enter your personal details on this page, they will
be stolen away.
Such an email is more than likely to be
the type of Internet scam known as “phishing”. Phishing is said to be
highly effective and has proved to have more success rate. This is
because, most Internet users are unaware of this type of attack and
hence fail to identify the scam.
Most legitimate companies never request
for any kind of personal/sensitive information via email. So, it is
highly recommended that you DO NOT respond to such fraudulent emails. For more information on phishing visit my detailed post on How to identify and avoid phishing scams?
2. Nigerian Scams:
This type of scam involves sending
emails (spam) to people in bulk seeking their help to access a large
amount of money that is held up in a foreign bank account. This email
claims that, in return for the help you’ll be rewarded a percentage of
the fund that involves in the transaction. Never respond to these emails
as it’s none other than a scam.
In case if you respond to these emails
you will be asked to deposit a small amount of money (say 1-2% of the
whole fund) as an insurance or as an advance payment for the
initialization of the deal. However, once you deposit the amount to the
scammer’s account you’ll not get any further response from them and you
lose your money. In fact, “The large amount of money” never exists and
the whole story is a trap for innocent people who are likely to become
victims. The scammers use a variety of stories to explain why they need
your help to access the funds. The following are some of the examples of
them:
Examples:
- They may claim that political climate or legal issues preclude them from accessing funds in a foreign bank account.
- They may claim that the person is a minor and hence needs your help to access the funds.
- They may claim that your last name is the same as that of the deceased person who owned the account and suggest that you act as the next of Kin of this person in order to gain access to the funds.
3. Lottery Scams:
This type of scam is similar to the one
discussed above. In this type, you may receive an email saying that you
have won a large sum of money in an online lottery scheme (ex. UK
Lottery) even though you have not participated in any such schemes. The
message claims that your email ID was selected randomly from a lagre
pool of IDs.
When you respond to such emails they
initially ask for your complete name and address so that they can mail
the cheque accross to you. After getting those details they may also
send you an image of the cheque drawn in your name and address so as to
confirm the deal. But in order to mail this cheque they demand a small
amount of money as insurance/shipping charge/tax in return.
However, if you send the money in a hope
to receive the cheque, all you get is nothing. You’re just trapped in a
wonderful scam scheme. That’s it.
4. Other General Scams and Frauds:
The following are some of the other types of scams that you should be aware of:
In general, be aware of unsolicited emails that:
- Promise you money, jobs or prizes.
- Ask you to provide sensitive personal information.
- Ask you to follow a link to a website and log on to an account.
- Propose lucrative business deals.
It may seem to be a difficult task for
the novice Internet user to identify such online scams. So, here are
some of the common signs of such scam emails. By knowing them it may
help you to stay away:
- All these scam emails never address you by your name. In turn they commonly address you something like “Dear User” or “Dear Customer” etc. This is a clear indication that the email is a fraudulent one.
- When you observe the email header you may notice in the “TO:” Field that, the same email is forwarded to a large group of people or the “TO:” field appears blank. So, this confirms that the email was not intended particularly for you. It was forwarded for a large group of people and you are one among them.
I hope this post helps. Express your opinion through comments.
How to Test the Working of Your Antivirus: EICAR Test
This process can be used by people,
companies and antivirus programmers to test the proper functioning of
the antivirus/antimalware software without having to deal with the real
computer virus which can cause damage to the computer.
How to Test Your Antivirus?
Here is a step-by-step procedure to test your antivirus functionality:
-
Open a notepad (New Text Document.TXT) and copy the following code exactly onto it, and save the notepad.EICAR Test codeX5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
-
Rename the file from “New Text Document.TXT” to “virus-sample.com”.
-
Now run the antivirus scan on this “virus-sample.com” file.
If the antivirus is working properly on
your computer, then it should generate a warning message and immediately
delete the file upon scanning. Otherwise, you may have to re-install
your antivirus.
NOTE: Most antivirus (with auto-detect feature) will pop-out a warning message in the Step-1 itself.
You can also place the
“virus-sample.com” file in a ZIP or RAR file and run a scan on it so as
to ensure that your antivirus can detect the test string even in the
compressed archive. Any antivirus while scanning this file should
respond exactly as it will do for a genuine virus/malicious code.
This test will cause no damage to your
computer even though the antivirus will flag it as a malicious script.
Hence, it is the safest method to test the proper functioning of any
antivirus software.
How EICAR Antivirus Test Works?
During the development of the antivirus
software, the AV programmers flag the EICAR test code/string as a
verified virus. This is a standard adopted by every antivirus company so
as to make the testing process simple and risk-free. Therefore, every
antivirus will respond to EICAR string in the same way it does for a genuine malicious code.
Top 25 People Who Changed the Internet Forever ---

1. Sir Tim Berners-Lee – World Wide Web
2. Vint Cerf And Bob Kahn – TCP/IP
3. Larry Page and Sergey Brin – Google Inc.4. David Filo and Jerry Yang – Yahoo! Inc.
5. Bill Gates – Microsoft
6. Steven Paul Jobs – Apple Inc.
7. Mark Zuckerberg – Facebook
8. Chad Hurley and Steve Chen – YouTube
9. Linus Torvalds – Linux
10. Jack Dorsey – Twitter
11. Kevin Rose – Digg
12. Bram Cohen – BitTorrent
13. Mike Morhaime – Blizzard Entertainment
14. Jimmy Wales – Wikipedia
15. Jeff Preston Bezos – Amazon
16. Shawn Fanning – Napster, Rupture
17. Pierre Omidyar – eBay
18. Jack Ma – Alibaba
19. Craig Newmark – Craigslist
20. Matt Mullenweg – WordPress
21. Thomas Anderson – MySpace
22. Garrett Camp – StumbleUpon
23. Jon Postel – Internet Pioneer
24. Caterina Fake – Flickr
25. Marc Andreessen – Netscape</div>
who search Ur Facebook account
its very to simply track . who search Ur Facebook account
............................
normal coding and find who serch ur facebook account
toggleTargetClosed="rfloat"><h3 class="accessible_elem">Privacy Shortcuts</h3><a class="_d1r uiHeaderActions" href="#" role="button"><i class="sp_6g6kqu sx_d4fbdb"><u>Search</uef="#" role="button" id="u_0_6"><i class="default sp_6g6kqu><div class="clearfix"><div class="lfloa
............................
normal coding and find who serch ur facebook account
toggleTargetClosed="rfloat"><h3 class="accessible_elem">Privacy Shortcuts</h3><a class="_d1r uiHeaderActions" href="#" role="button"><i class="sp_6g6kqu sx_d4fbdb"><u>Search</uef="#" role="button" id="u_0_6"><i class="default sp_6g6kqu><div class="clearfix"><div class="lfloa
Subscribe to:
Comments (Atom)



























